Ssh_exchange_identification Read Connection Reset by Peer Drupal
Introduction
A remote motorcar has prevented an SSH connection yous were attempting to establish or maintain. The "ssh_exchange_identification: read: Connectedness reset by peer" message is not specific enough to immediately explain what triggered the error.
To be able to resolve the issue successfully, nosotros first demand to identify its crusade. This article provides an in-depth analysis of the likely causes and provides the most effective solutions.
By reading this tutorial, yous will acquire how to fix the "ssh_exchange_identification: read: Connection reset by peer" Error.
Prerequisites
- Necessary permissions to access remote server
- A user account with root or sudo privileges
What Causes the "Connexion reset by peer" SSH Mistake?
The "ssh_exchange_identification: read: Connection reset by peer" error indicates that the remote car abruptly closed the Transition Control Protocol (TCP) stream. In most instances, a quick reboot of a remote server might solve a temporary outage or connectivity consequence.
Note: Network-based firewalls or load-balancers tin sometimes distort IPs or security permissions. This type of problem can be resolved by contacting your service provider.
Learning how to troubleshoot this issue, and determining the underlying crusade, helps you lot prevent futurity occurrences on your system. The most mutual causes of the "ssh_exchange_identification: read: Connection reset past peer" error are:
- The connexion is being blocked due to the Host-Based Access Command Lists.
- Intrusion prevention software is blocking your IP by updating firewall rules (Fail2ban, DenyHosts, etc.).
- Changes to the SSH daemon configuration file.
Cheque the hosts.deny and hosts.allow File
The hosts.deny and hosts.allow files are TCP wrappers. As a security feature, these files are used to limit which IP address or hostname can institute a connection to the remote machine.
Annotation: Inspect the hosts.deny and hosts.allow files on the remote server, not on the local client.
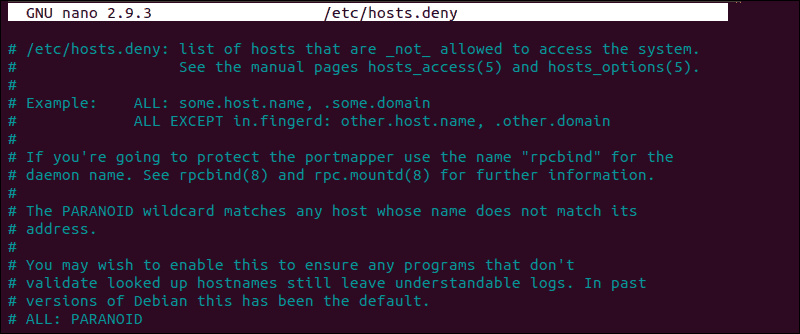
How to Edit hosts.deny File
Access your remote server and open up the hosts.deny file using your preferred text editor. If y'all are using nano on a Debian based system, enter the following command:
sudo nano /etc/hosts.deny Empty lines and lines starting with the '#' symbol are comments. Bank check if you can locate your local IP or host-name in the file. If it is present, information technology should be removed or commented out, or else it prevents you from establishing a remote connectedness.
Subsequently making the necessary changes, salve the file and exit. Endeavour to reconnect via SSH.
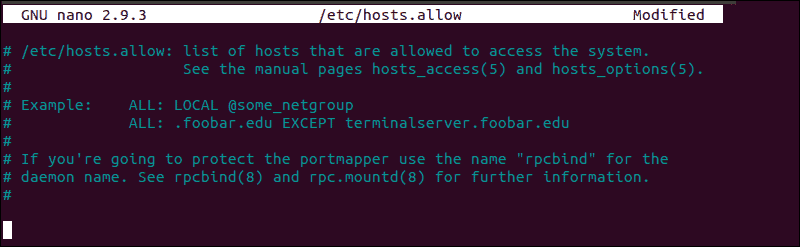
How to Edit hosts.allow File
As an boosted precaution, edit the hosts.allow file. Access rules within the hosts.allow are practical first. They take precedence over rules specified in hosts.deny file. Enter the following command to access the hosts.allow file:
sudo nano /etc/hosts.allow Calculation host-names and IPs to the file defines exceptions to the settings in the hosts.deny file.
For case, a strict security policy inside the etc/hosts.deny file, would deny access to all hosts:
sshd : ALL ALL : ALL Subsequently, you can add a single IP accost, an IP range, or a hostname to the etc/hosts.allow file. By adding the post-obit line, only the post-obit IP would be allowed to establish an SSH connection with your remote server:
sshd : 10.10.0.five, LOCAL Go along in mind that such a limiting security setting can affect administering capabilities on your remote servers.
Check if fail2ban Banned Your IP Address
If you've tried to connect on multiple occasions, your IP might be blocked by an intrusion prevention software. Fail2ban is a service designed to protect you lot from animal force attacks, and it can misinterpret your hallmark attempts as an attack.
Fail2ban monitors and dynamically alters firewall rules to ban IP addresses that showroom suspicious behavior. It monitors logs, like the hosts.deny and hosts.allow files we edited previously.
In our example, nosotros used the following control to check if the iptables tool is rejecting your attempted connections:
sudo iptables -L --line-number The output in your terminal window is going to list all authentication attempts. If you lot find that a firewall is indeed preventing your SSH connectedness, you tin can white-list your IP with fail2ban. Otherwise, the service is going to block all future attempts continuously. To access the fail2ban configuration file, enter the following command:
sudo nano /etc/fail2ban/jail.conf Edit the file by uncommenting the line that contains "ignoreip =" add the IP or IP range you lot want to white-list.
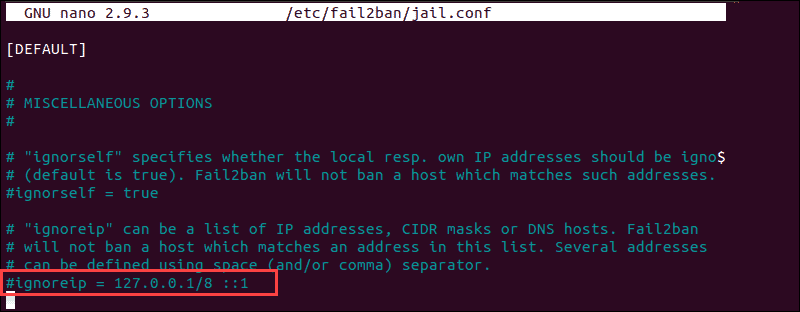
Fail2ban is now going to make an exception and not report suspicious behavior for the IP in question.
Check the sshd_config File
If you are continuing to feel the 'ssh_exchange_identification: read: Connection reset past peer' mistake, examine the authentication log entry. By default, the SSH daemon sends logging data to the system logs. Admission the /var/log/auth.log file after your failed attempt to login. To review the latest log entries type:
tail -f /var/log/auth.log The output presents the results of your hallmark attempts, information about your user account, authentication key, or password.
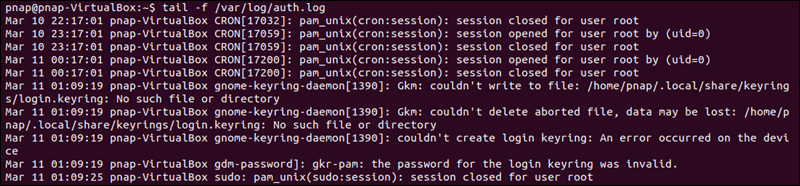
The log provides you with information that can help y'all find possible bug in the sshd configuration file, sshd_config. Any changes made to the file can touch on the terms under which an ssh connection is established and lead the remote server to treat the client as incompatible. To access the sshd_config file type:
sudo nano /etc/ssh/sshd_config The sshd configuration file enables you to change basic settings, such equally the default TCP port or SSH cardinal pairs for authentication, likewise as more than advanced functions such every bit port-forwarding.
For example, the MaxStartups variable defines how many connections a system accepts in a predefined period. If you have a system that makes a large number of connections in a short timeframe, it might be necessary to increase the default values for this variable. Otherwise, the remote system might reject boosted attempted ssh connections.

Anytime you edit the sshd_config file, restart the sshd service for the changes to take effect:
service sshd restart But edit the variables that yous are familiar with. A server tin can become unreachable every bit a effect of a faulty configuration file.
Conclusion
Yous have thoroughly checked the most common reasons backside the "ssh_exchange_identification: read: Connection reset by peer" fault. Past looking at each possibility, in plough, you lot have successfully solved the consequence and now know how to deal with similar issues going forward.
The number of potential causes is vast and difficult to troubleshoot in every respect. Ultimately, if the error persists, it might exist necessary to contact your host.
Was this article helpful?
Aye No
Source: https://phoenixnap.com/kb/fix-connection-reset-by-peer-ssh-error
0 Response to "Ssh_exchange_identification Read Connection Reset by Peer Drupal"
Post a Comment